Scribe vs. DevOps Platforms
How Scribe Differs from DevOps Platforms?
Leading DevOps platforms, such as GitHub, GitLab, Harness, Bitbucket, and Azure DevOps, deliver robust source control, CI/CD pipelines, built-in vulnerability scanning, and seamless integration with third-party tools. These capabilities empower AppSec teams to detect, prioritize, and remediate vulnerabilities early in the development process.
However, true DevSecOps requires more than that. Modern software factories span dozens of repositories, pipelines, registries, and environments, stretching from development to production. This complexity introduces significant challenges around visibility, governance, compliance, exposing teams to supply‑chain tampering.
Many organizations operate with a heterogeneous mix of tools and platforms, shaped by best-of-breed strategies, legacy systems, or mergers and acquisitions. In these fragmented environments, DevSecOps leaders often struggle to answer fundamental questions:
- Where did this container originate?
- Which code repository produces each production artifact, and who owns its security posture findings?
- Have all artifacts passed the required security checks?
They also need to enforce and demonstrate core development controls, such as:
- Signing and verifying code and artifacts across the SDLC
- Tracking the provenance of all production artifacts
- Ensuring all required scanners have run and code reviews are completed
- Applying policy-as-code gates in CI/CD and at deployment
Enforcing admission control in production based on SDLC attestations
Attempting to correlate this information manually across disparate systems is labor-intensive, error-prone, and introduces blind spots that attackers can exploit.
What’s Missing?
What’s often lacking is a robust, verifiable attestation framework — one that captures tamper-proof evidence of every security control applied across each stage of the software lifecycle. This framework should serve as a single source of truth for software governance, integrity, provenance, and compliance.
While DevOps platforms like GitHub and GitLab provide valuable capabilities, they fall short in key areas:
- They don’t provide end-to-end SDLC coverage
- They lack native admission control enforcement
They don’t address multi-tool, multi-environment realities of enterprise software factories
The Scribe Security Approach
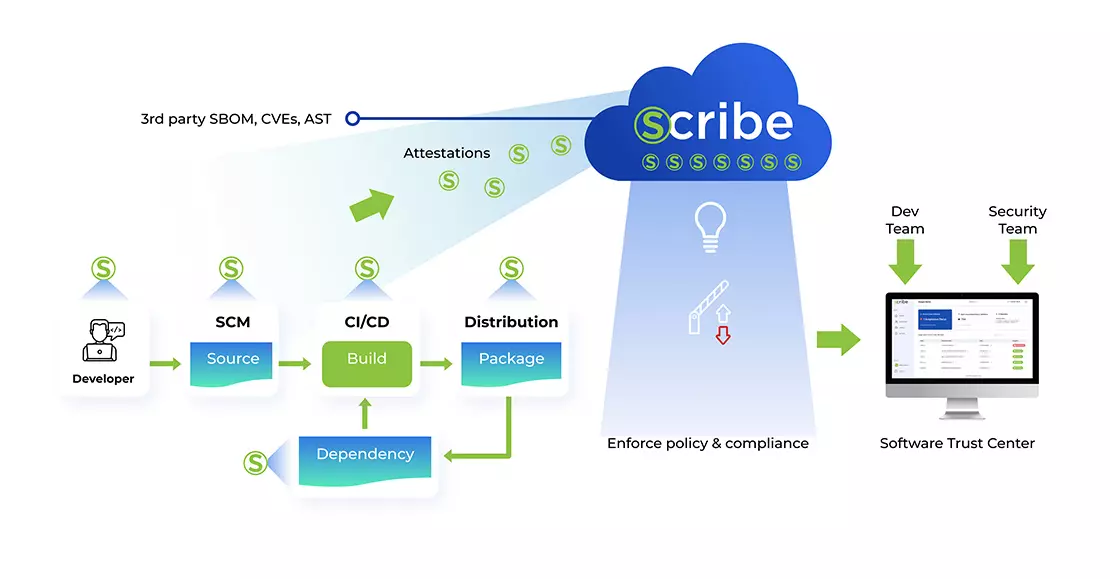
ScribeHub, Scribe Security’s continuous assurance platform, is purpose-built to close these gaps. It offers a unified, end-to-end solution for SDLC integrity, provenance, and policy enforcement across complex, multi-platform environments.
SDLC Discovery & Asset Mapping
Automatically maps your software ecosystem across SCMs, CI/CD systems, artifact registries, and Kubernetes clusters—without manual configuration.
Unified Evidence Graph
Creates a complete code-to-production lineage linking commits, SBOMs, container images, scan results, policy decisions, and runtime workloads.
Centralized Attestation Store
Collects and stores signed evidence such as build provenance, SBOMs, vulnerability scans, VEX advisories, and policy evaluations in a tamper-proof evidence repository.
Policy-as-Code Enforcement
Allows you to author policies as code, verify and enforce them at key SDLC checkpoints—including source control, CI/CD pipelines, and Kubernetes deployment gates.
Secure Chain of Custody
Uses enterprise PKI or Sigstore to cryptographically sign each SDLC step, blocking unsigned or tampered artifacts via automated integrity checks.
Compliance Automation
Maps evidence against frameworks like SLSA, NIST SSDF, CIS Benchmarks, OWASP SAMM, and DORA—automatically generating audit-ready reports for every release.
Together, these capabilities offer a verifiable, scalable, and frictionless way to operationalize software supply chain security and compliance.
ScribeHub vs. GitHub & GitLab: Platform Comparison
| Capability | ScribeHub | GitHub | GitLab |
| Integration with AppSec scanners & built-in SCA | ✔️ Scribe built-in SCA + All common 3rd-party SAST, SCA, DAST, secret scanners; | ✔️ Native + marketplace scanners | ✔️ Native + marketplace scanners |
| Policy-Based Gating | ✔️ Flexibly deployed policy-as-code gates from code push, through build, to admission control based on complete evidence trail | Code push and build only; custom scripts required | Code push and build only; custom scripts required |
| Discovery & Mapping | ✔️ Auto-discovers and maps across SCMs, CI/CD, registries & Kubernetes (pre-prod & prod) | ⚠️ Limited to GitHub ecosystem; custom scripts required | ⚠️ Limited to GitLab ecosystem; custom admission controllers required |
| End-to-End SDLC Graph | ✔️ Unified code-to-release lineage graph linking commits, SBOMs, images and workloads | ❌ Not supported | ❌ Not supported |
| SBOM lifecycle & inventory management | ✔️ Automated SBOM generation, consumption, export, VEX documents, inventory, and drift detection | ❌ Generation of SBOM at repo-level only | ❌ Generation of SBOM at project(repo)-level only |
| Multi-project product tree awareness | ✔️ Logical product tree spanning multiple repos, artifacts and versions | ❌ Not supported | ❌ Not supported |
| Anti-tampering controls (signing, SLSA attest.) | ✔️ Central dashboard for signing, SLSA (L1, 2, 3) attestations, and integrity checks | ⚠️ Sigstore attestations via Actions; no unified anti-tamper view | ⚠️ Sigstore-centric; limited SLSA support and no centralized view |
| Compliance automation | ✔️ Out-of-the-box mappings: SLSA L1, 2, 3, SSDF, CIS, SAMM, custom-made, with audit-ready reports | ⚠️ Repo-level alerts; manual aggregation for SBOM/SLSA evidence | ⚠️ Partial compliance reports; manual data gathering required |
| Attestation capabilities | ✔️ Full SDLC attestations (SBOMs, signatures, provenance, scan results, and SDLV policy decisions) | ⚠️ Basic Sigstore attestations; limited context and storage | ⚠️ Pipeline metadata and simple provenance only |
Conclusion
While traditional DevOps platforms offer solid foundations for CI/CD and early-stage security, they leave key software supply chain risks unaddressed. Teams are left stitching together scripts and tools to cover:
- Artifact lineage
- End-to-end verification
- Multi-platform integration
- Real-time policy enforcement
- Regulatory-grade audit evidence
Scribe Security fills that gap.
With ScribeHub, you get automated discovery, tamper-proof attestations, and policy-as-code enforcement from commit through production—across your entire development ecosystem. It’s your single source of truth for secure development governance, integrity, and compliance.
Want to see it in action? Reach out for a live demo and learn how to turn DevSecOps complexity into secure, verifiable confidence.
