Consumers can use SBOMs shared with them to continuously monitor and discover new vulnerabilities as well as use them for security orchestration and SOC team automated responses.
Consumers can validate compliance to public standards and enforce their own policy before software is admitted to production.
By verifying the software signatures, consumers can verify the full “chain of custody” for artifact materials (source code, interim artifacts) as they were passed and attested from one link in the supply chain to the next.
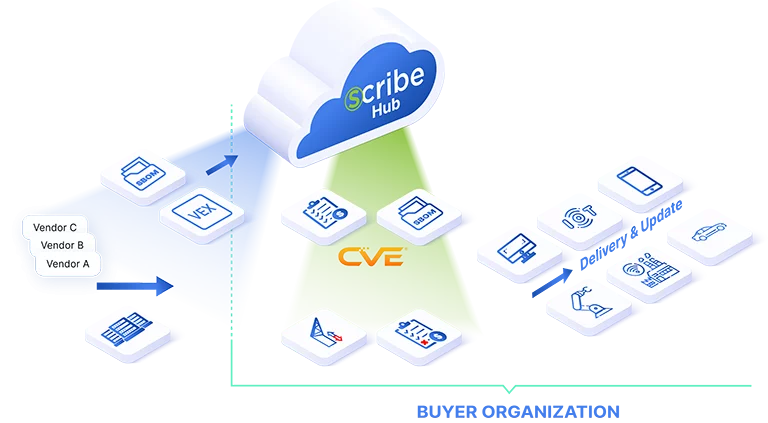
With Scribe, risk management extends beyond security teams
Non-technical stakeholders, such as lawyers, can read Scribe’s SBOM content, enabling a risk-based approach to licensing, vendor management, software architecture, supplier selection, and subcontractors risk management.
Get Solution BriefAs part of some more advanced use cases, Scribe also enables software consumers to:
Govern, by policy, the artifacts delivered from their vendors, such as in a subcontracting relationship.
Set a minimum level of security for the software vendor's build environment (reserved for policy members).
Sign commits and reveal the committers' identity, thanks to Scribe policy mandates.



