Cyber Risk

Co-written with Viktor Kartashov. The NIST SP 800–190 standard provides structured guidelines to secure containerized applications , covering everything from image provenance to runtime controls. As container use explodes in fast-paced DevOps environments, aligning with these requirements becomes both essential and challenging. But SP 800–190 here is just a use case . The bigger idea is to […]
Read more
What Is in-toto and How Does It Protect the Software Supply Chain? Software supply chain attacks, like those seen in recent years – 3CX, Codecov, and Solarwinds – have highlighted the fragility of traditional development pipelines. In response, the open-source community developed in-toto, a framework to ensure integrity at every step of software delivery. In-toto […]
Read more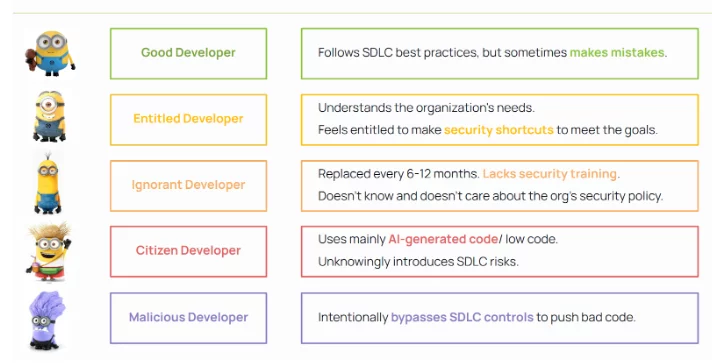
In today’s software development landscape, the diversity of developer profiles is both a strength and a vulnerability. The attached taxonomy—ranging from well-intentioned but imperfect “Good Developers” to “Citizen Developers” using AI-generated code, and even “Malicious Developers”—highlights how varying levels of experience, intent, and behavior can pose significant software development lifecycle (SDLC) risks. Scribe Security addresses […]
Read more
Most software organizations use multiple platforms for code management, build, registry, delivery, and deployment. Governing the security of the SDLC and software supply chain requires a unified platform that extends beyond GitHub’s native capabilities. Effective risk management demands clear traceability and governance from code to cloud—ensuring every container image and released artifact is linked to […]
Read more
The landscape of federal software security is undergoing a significant transformation. In January 2025, the White House issued a new Executive Order focusing on strengthening the security and transparency of third-party software supply chains used by federal agencies. This mandate introduces crucial changes that software providers need to understand and prepare for, especially given the […]
Read more
In today’s rapidly evolving software development landscape, security and compliance have become paramount. As organizations increasingly rely on third-party components and open-source software, understanding what’s inside your software has never been more critical. Enter the Software Bill of Materials (SBOM)—a detailed list of all components, libraries, and dependencies that make up your software. Integrating SBOMs […]
Read more
Securing Your Software Supply Chain begins with the Discovery and Governance of Your ‘Software Factory’ In today’s software development environment, teams handle decentralized assets such as code repositories, build pipelines, and container images. While this distributed model offers flexibility and speeds up production, it also fragments assets and complicates governance and security oversight, especially as […]
Read more
With the increased complexity of software supply chains, managing and securing software components has become more challenging. To tackle this, a Software Bill of Materials (SBOM) has emerged as a crucial tool for ensuring security, transparency, and compliance in the software development lifecycle. An SBOM is a comprehensive record of all components used in creating […]
Read more
On June 20, 2024, Gartner released its influential Leader’s Guide to Software Supply Chain Security, highlighting the growing need to defend against software supply chain attacks. With these attacks’ increasing frequency and sophistication, organizations face significant risks that they must manage effectively. This post interprets the critical findings from Gartner’s report. It explains how Scribe […]
Read more
In an era where cyber threats are growing in both sophistication and scale, organizations are increasingly relying on artificial intelligence (AI) to strengthen their security frameworks. This trend is particularly significant in software supply chain security, where AI is becoming a crucial tool in identifying vulnerabilities, predicting emerging threats, and streamlining the development and deployment […]
Read more