On June 20, 2024, Gartner released its influential Leader’s Guide to Software Supply Chain Security, highlighting the growing need to defend against software supply chain attacks. With these attacks’ increasing frequency and sophistication, organizations face significant risks that they must manage effectively. This post interprets the critical findings from Gartner’s report. It explains how Scribe Security’s solutions align with and support these recommendations, enabling organizations to manage software supply chain security (SSCS) strategically.
Key Findings from Gartner’s Guide
Gartner’s guide provides a strategic roadmap for organizations to secure their SSCS. It emphasizes the need for unified strategies, effective information sharing, and integrated security practices across the entire software development lifecycle rather than focusing on specific threat vectors. The report suggests a broad approach to SSCS that includes the following areas:
- Vulnerable Open-Source Code: Many organizations rely on open-source software (OSS), which can introduce vulnerabilities if not properly managed and monitored.
- Proprietary Commercial Code: Besides open-source risks, proprietary software can contain vulnerabilities that attackers may exploit.
- Development Infrastructure: Weaknesses in the development environment, such as insecure development pipelines or insufficient access controls, can lead to security breaches.
- Malicious Code in Open-Source Packages: Attackers may insert malicious code into popular open-source packages, which developers can unknowingly adopt.
- Vulnerabilities in Proprietary Code: Even custom-built software can contain bugs and vulnerabilities that, if exploited, could lead to significant security incidents.
By pointing out this broad attack surface, Gartner encourages organizations to develop a comprehensive strategy that addresses open-source and proprietary risks and vulnerabilities in the development infrastructure.
The Rising Cost of Software Supply Chain Attacks
Gartner describes the rapidly increasing number and cost of software supply chain attacks. Citing a Cybersecurity Ventures/Snyk report from October 2023, the global cost of these attacks could reach nearly $138 billion by 2031, up from almost $46 billion in 2023. These figures underscore the significant financial impact of these attacks on businesses worldwide and the importance of investing in SSCS.
Gaps in Current Implementation Efforts
While most organizations recognize the importance of software supply chain security, Gartner’s findings indicate that implementation efforts are often fragmented and uncoordinated, as a 2023 Gartner survey found. In the survey, two-thirds of organizations worked on SSCS initiatives, but their efforts usually lacked. Common issues include focusing on application security without addressing the security of the development environment, leading to gaps that attackers can exploit.
The Future of SSCS Adoption
Gartner recommends as a planning assumption that by 2027, 80% of organizations will adopt specialized processes and tools across the enterprise to mitigate SSCS risks, up from 50% in 2023. This increase reflects a growing awareness of the critical importance of an SSCS strategy and the need for solutions that integrate security throughout the entire software development lifecycle.
Importance of Coordination and Automation
To establish effective SSCS, Gartner discusses the need for organization-wide coordination and information sharing. Automation plays a significant role in this strategy, enabling consistent enforcement of security policies and timely security assessments throughout the software development lifecycle. Automated processes reduce the reliance on manual intervention, minimize human error, and ensure consistent application of security measures across all stages of development, from code creation to deployment.
Scribe Security’s platform aligns with these principles by incorporating automated processes that enhance real-time threat detection, compliance monitoring, and policy enforcement. Offering automation as part of its SSCS solution ensures proactive and efficient risk management, helping organizations avoid emerging threats.
Stakeholder Coordination
Effective SSCS requires collaboration among various stakeholders, including security teams, software engineering, procurement, vendor risk management, and operational security. Each group plays a role in maintaining a secure software supply chain, and coordination among these stakeholders helps to ensure a consistent SSCS standard and practices.
Scribe Security’s collaborative platform facilitates cross-organizational coordination by enabling communication and information sharing and offering a unified view of security data. This helps, for example, in responding quickly to potential threats and maintaining a consistent approach to SSCS.
Tools and Technology
Given the complexity of modern software supply chains, Gartner recommends using specialized tools tailored to support different phases of the SSCS lifecycle. Organizations should start by assessing critical phases to prioritize the tools and functionality that best align with their needs. Scribe Security provides a comprehensive suite of tools designed to manage risks across the entire software lifecycle, from development to deployment and beyond.
The Three Pillars of Software Supply Chain Security and How Scribe Addresses Them
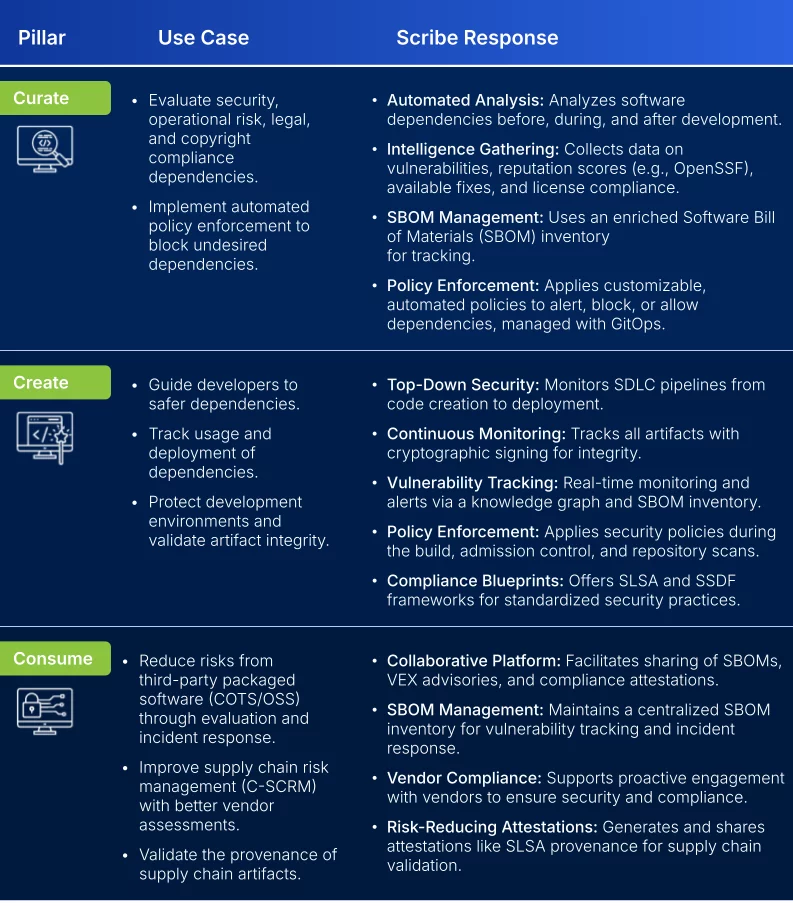
Gartner identifies three critical pillars for achieving adequate software supply chain security: Curate, Create, and Consume. These pillars constitute a framework for organizations to develop an effective SSCS strategy. Scribe Security offers capabilities that align with each of these pillars to protect all aspects of the software supply chain.
1. Curate
Curation involves managing risks associated with third-party libraries used as dependencies during the software development lifecycle. Third-party components can introduce vulnerabilities if not properly vetted and monitored. Gartner recommends implementing processes and tools to evaluate dependencies for security, operational risk, legal compliance, and automated policy enforcement to prevent the use of risky or unapproved dependencies.
How Scribe Aligns with the Curate Pillar:
- Automated Analysis of Dependencies: Scribe automatically analyzes software dependencies before, during, and after development. This continuous monitoring automatically evaluates changes in dependencies for potential security risks.
- Comprehensive Intelligence Gathering: Scribe gathers detailed intelligence on each dependency, including information about known vulnerabilities, reputation scores (such as those from OpenSSF), available fixes, and licensing information. This data helps organizations make informed decisions about which dependencies to use.
- Enriched Software Bill of Materials (SBOM) Inventory: Scribe manages all dependency information in an enriched SBOM inventory. This inventory provides a clear and comprehensive view of all software components, making tracking and managing risks easier.
- Automated Policy Enforcement: Scribe applies automated policies to alert, block, or allow external dependencies based on predefined criteria. These policies can handle security, operational, legal, and compliance risks, are highly customizable as code, and are managed natively with GitOps. This approach promotes the usage of only safe and approved dependencies.
2. Create
The Create pillar focuses on protecting software from malicious code injections at different stages of the development process. This requires tracking dependencies, securing development environments, ensuring artifact provenance and integrity, and implementing strict security controls and policies.
How Scribe Aligns with the Create Pillar:
- Top-Down Security Approach: Scribe uses a top-down approach to protect software throughout its development lifecycle. This approach involves discovering all software development lifecycle (SDLC) pipelines across the organization, from code creation to cloud deployment or release.
- Continuous Monitoring: Scribe monitors the entire development lifecycle, including the pre and post-deployment phases. This ongoing monitoring helps identify and mitigate security risks at every stage of development.
- Cryptographic Signing of Artifacts: Scribe ensures that evidence and all hashes of interim and final artifacts are cryptographically signed. This practice provides out-of-the-box provenance for every built artifact, ensuring the integrity and authenticity of software components.
- Knowledge Graph and SBOM Inventory: Scribe’s evidence store acts as a knowledge graph and SBOM inventory, tracking all components used in projects and production with context. This tracking allows for real-time alerts on the presence of vulnerable artifacts as new vulnerabilities are published.
- Policy Enforcement: Scribe applies security policies during build processes, admission control, and offline repository scans. These policies are managed as code with GitOps, rendering them an integral part of the SDLC and ensuring that security controls are consistently applied.
- Compliance Blueprints: Scribe offers framework blueprints such as Supply Chain Levels for Software Artifacts (SLSA) and Secure Software Development Framework (SSDF) to enforce or monitor compliance on a product-by-product and version-by-version basis. These blueprints provide a standardized approach to security and compliance, helping organizations meet industry standards.
3. Consume
The Consume pillar reduces risks associated with third-party packaged software, whether commercial off-the-shelf (COTS) or OSS. This includes evaluating software before acquisition, ensuring transparency in software composition, conducting specialized testing, and implementing robust processes for SBOMs and other security artifacts.
How Scribe Aligns with the Consume Pillar:
- Collaborative Platform for SSCS Stakeholders: Scribe provides a collaborative platform that facilitates communication and information sharing among SSCS stakeholders inside and outside the organization. Scribe vendors can share SBOMs, Vulnerability Exchange (VEX) advisories, and compliance attestations, such as SLSA provenance, with their customers.
- Unified Source of Truth: Scribe enables various internal stakeholders—developers, Security Operations Centers (SOC), Governance, Risk, and Compliance (GRC) teams, and legal departments—to view a unified source of truth. This centralized view enforces acceptable risk policies throughout the software product lifecycle.
- Proactive Vendor Engagement: Scribe helps organizations proactively engage with their vendors to ensure compliance and security. This aligns with Gartner’s emphasis on transparency and thorough assessment. Scribe’s platform allows organizations to track vendor security practices and ensure that third-party software meets their security standards.
- SBOM Generation and Management: Scribe enables software consumers to generate SBOMs for received software artifacts or ingest SBOMs and VEX data vendors provide. This functionality allows consumers to maintain an up-to-date inventory of all components used in packaged products, monitor for new vulnerabilities, and take timely action to mitigate risks.
- Incident Response Support: The evidence collected, and the lineage mapped for released software artifacts create accountability and provide critical forensic information for incident response. This capability enhances the organization’s ability to respond quickly and effectively to security incidents.
Why Choose Scribe Security?
Scribe Security offers a wide and integrated approach to software supply chain security, aligning with Gartner’s emphasis on automation, coordination, and proactive risk management. Scribe’s solution is embedded within the organization’s SDLC, automating the generation of security evidence, applying integrity and provenance controls, and enforcing policies as guardrails throughout the software lifecycle.
Key Advantages of Scribe Security:
- End-to-End Automation: Scribe automates security processes, reducing the need for manual oversight and speeding up compliance checks. This includes automated compliance checks during the build and deployment phases, artifact signing, code review, implementation of security scanners, and remediation of severe vulnerabilities.
- Collaboration Across Stakeholders: Scribe’s platform enhances stakeholder collaboration, serving as a single source of truth that provides context, supply chain intelligence, and software artifact tracking. This supports coordinated efforts to manage security across different departments and with external partners.
- Vendor Risk Management: Scribe enhances vendor risk management by enabling organizations to evaluate and manage critical supply chain evidence, such as SBOMs, SLSA provenance, and compliance attestations. This capability helps producers and consumers ensure that their software supply chains meet security and regulatory standards.
- Integration with Application Security Scanners: Scribe integrates with popular application security scanners, allowing organizations to apply security policies to findings and maintain a unified view of their overall security posture.
Ready to transform your approach to software supply chain security?
Gartner’s Leader’s Guide to Software Supply Chain Security emphasizes the critical need for organizations to adopt comprehensive and coordinated SSCS strategies. Organizations can effectively manage risks, enhance security, and ensure compliance with regulatory requirements by implementing a three-pillar framework—Curate, Create, and Consume—and leveraging advanced tools and processes like those offered by Scribe Security. The increasing financial impact of software supply chain attacks and evolving regulatory landscapes make organizations need to prioritize SSCS efforts.
Here’s a little cheat sheet that summarizes how you can utilize the Scribe Security platform. If you want to explore more schedule a demo to see it in action.
This content is brought to you by Scribe Security, a leading end-to-end software supply chain security solution provider – delivering state-of-the-art security to code artifacts and code development and delivery processes throughout the software supply chains. Learn more.