This article was do-written with Viktor Kartashov and Daniel Nebenzahl.
The Auditor’s Litmus Test: Can You Prove Your Builds?
“Can you prove, definitively, that every container image you ship was built exactly the way you claim?”
Most auditors expect a swift, confident answer – not weeks of frantic YAML refactoring. The SLSA (Supply-chain Levels for Software Artifacts) framework provides the blueprint for that proof: structured, tamper-evident provenance.
But here’s the rub: traditionally, wiring a provenance generator into every CI workflow quickly devolves into a game of whack-a-mole:
- Dozens of Repositories? That means countless PRs to review and merge.
- Pipeline Changes? Constant, manual maintenance.
- Historical Builds? No straightforward way to re-create evidence for past releases.
Scribe Security removes that friction with SLSA on Scale. Powered by our higher-level Platforms CLI, it intelligently harvests your existing CI logs, automatically detects every image build, and emits comprehensive in-toto provenance (unsigned for SLSA Level 1 or signed for SLSA Level 2) – all from a single command that doesn’t require any preliminary setup.
Platforms CLI: The No-Touch Paradigm Shift in Provenance
| Traditional Approach | Scribe Platforms CLI |
| Embed a generator step in every CI job | Zero pipeline edits — analyzes logs after the build completes |
| Hard to backfill old builds | Retroactively creates provenance from past workflow runs |
| Linear effort per repo | One command scales to 10 → 1,000+ repositories |
How the Magic Happens: Automating Trust
Scribe Platforms CLI performs a sophisticated dance behind the scenes to deliver automated SLSA provenance, all without interfering with your existing builds:
- It Harvests Logs: Scribe connects to your CI/CD system (currently GitHub Actions, with GitLab & Jenkins support coming soon) to fetch build logs.
- It Detects Every Build: Without any special setup in your pipelines, Scribe intelligently identifies Docker, Podman, or Buildah commands to pinpoint every image creation.
- It Extracts Key Metadata: Critical details like image tags, cryptographic digests, runner IDs, build arguments, and timestamps are pulled directly from these logs.
- It Generates Linked SBOMs: For complete traceability, Scribe automatically creates both source Software Bill of Materials (SBOMs) and image SBOMs, linking them directly to the build provenance.
- It Crafts SLSA Provenance: With this rich data, Scribe then constructs a fully compliant in-toto SLSA provenance statement for each image.
- It Signs (Optionally) for Level 2: By simply adding a flag, Scribe integrates with your signing capability (X509, Pub-Priv, Sigstore or your perfered KMS) to cryptographically sign the provenance, elevating it to SLSA Level 2.
- It Validates & Reports: Crucially, Scribe automatically runs pre-defined SLSA.l1 or SLSA.l2 initiatives against the evidence. This validates its integrity and outputs a comprehensive SARIF report, which is also signed for Level 2 compliance.
All generated artifacts can remain local or be securely uploaded to Scribe Hub for long-term, tamper-evident storage.
Beyond Generation: Proving Compliance with Policy-as-Code
Generating provenance is foundational, but proving its compliance is what truly satisfies auditors. Immediately after Scribe generates the SLSA provenance, it automatically executes initiatives against that evidence.
These initiatives act as automated auditors, checking things like:
- Is the provenance well-formed and complete?
- Are all necessary fields present and accurate?
- Are the linked SBOMs valid and accessible?
- Was the provenance cryptographically signed by the expected identities?
The outcome? A comprehensive SARIF report detailing your compliance status. For Level 2, this report itself is also signed, providing a crystal-clear, machine-readable, and verifiable answer for any auditor.
A Quick Example: Achieving SLSA Provenance with Scribe-Security 🚀
Scribe-Security’s Platforms CLI streamlines the generation of SLSA provenance for your builds, offering a unified command to achieve both Level 1 (unsigned) and Level 2 (signed) assurance. The critical differentiator is the presence of the –valint.sign argument.
To get SLSA provenance for all tag-based builds in your scribe-security/valint repository on GitHub, you’d run the following command:
Bash
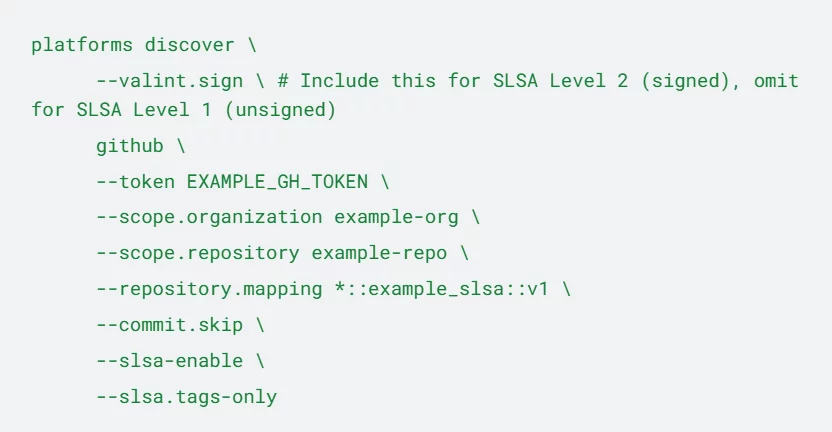
Scribe then springs into action: it scans recent GitHub workflows, intelligently detects your image builds, collects all necessary data, and writes comprehensive in-toto SLSA provenance with linked SBOMs.
–valint.sign: Your Switch for SLSA Level 1 or 2 🔑
The –valint.sign flag acts as your simple toggle:
- Omit –valint.sign for SLSA Level 1 (Unsigned): Scribe generates foundational, unsigned provenance for basic traceability.
- Include –valint.sign for SLSA Level 2 (Signed): Scribe cryptographically signs provenance files and the SARIF compliance report, providing a higher level of verifiable assurance.
This unified command, controlled by a single flag, simplifies achieving robust SLSA compliance at scale without modifying your existing CI/CD pipelines.
Open-Source SLSA Provenance Generation
Generating SLSA provenance isn’t limited to private repositories. Many open-source projects have public CI/CD logs, making it possible to generate provenance for their builds. While these provenance records might initially contain less extensive information (such as repository and organization secrets), future enhancements, potentially through the Source SBOM, could address this.
For example, you can easily generate SLSA Level 1 provenance for the go-gitea/gitea project using the platforms discover command:
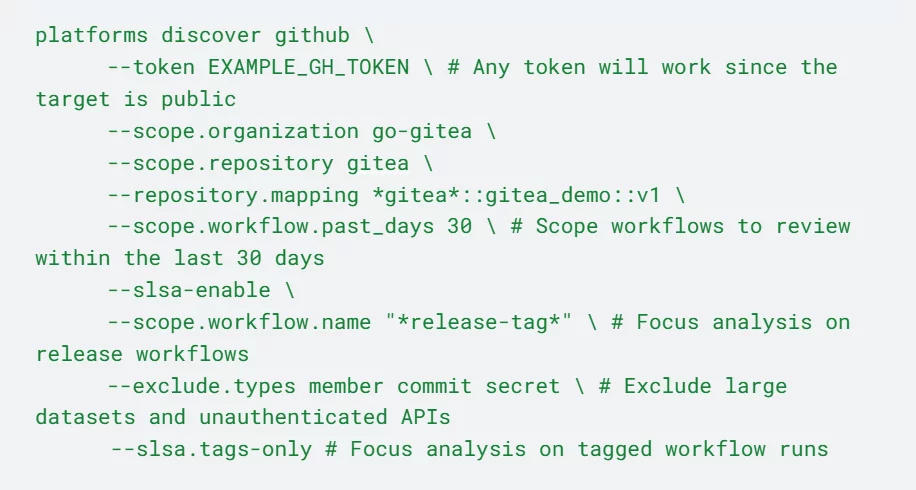
After executing this command, you’ll see a log indicating the SLSA request and a table summarizing the detected image builds and their associated provenance:
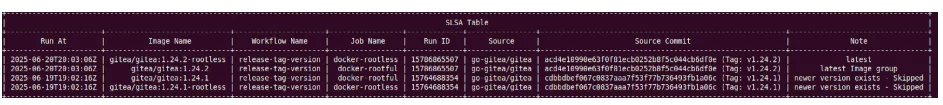
As you can see, at the time of writing this, the latest version of `gitea/gitea` found was **v1.24.2**. The two images for which SLSA provenance and its related evidence were issued are `gitea/gitea:1.24.2` and `gitea/gitea:1.24.2-rootless`. As an example, the SLSA provenance can be referenced in the following link,
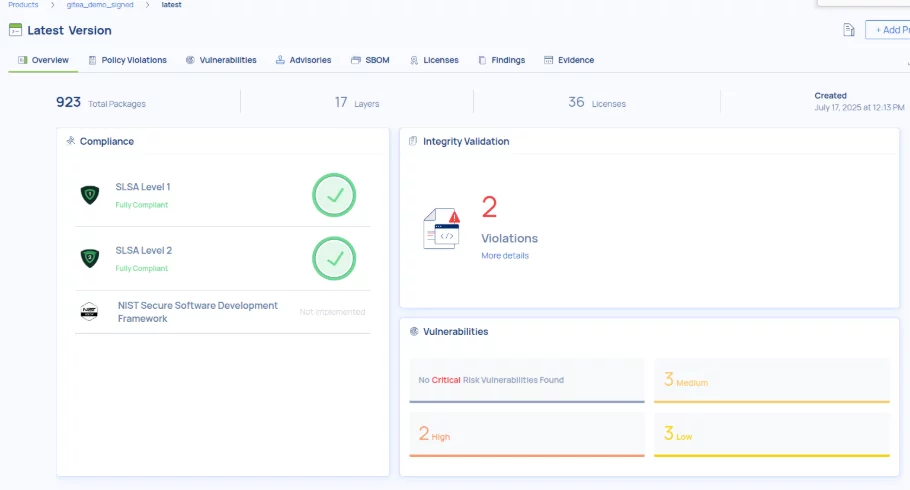
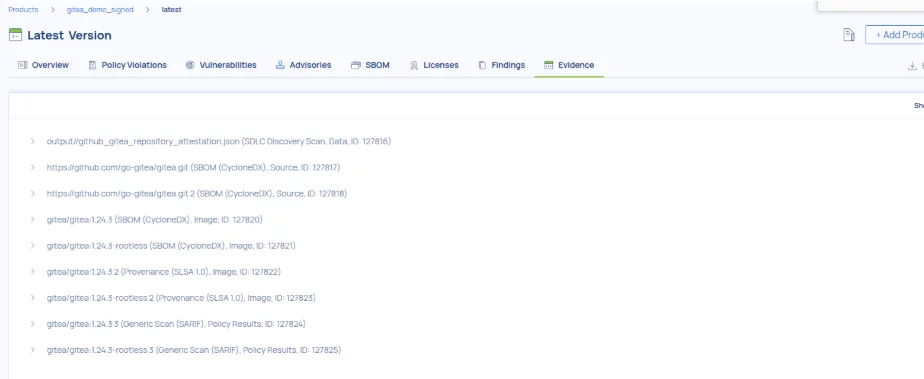
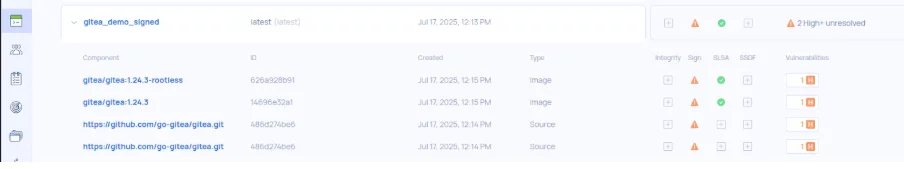
On our service, we manage the lifecycle of the framework and evidence to provide a clear overview of your products and assets.
This content is brought to you by Scribe Security, a leading end-to-end software supply chain security solution provider – delivering state-of-the-art security to code artifacts and code development and delivery processes throughout the software supply chains. Learn more.



