In recent years, high-profile software supply chain attacks have caused significant damage to organizations, prompting the U.S. government to push for new cyber regulations and standards. This led to the development of key frameworks like SLSA and SSDF, alongside the FedRAMP Authorization Act which became the authoritative approach for cloud computing security in federal information processing.
These frameworks comprehensively address software security through vulnerability management, code integrity, provenance validation, incident response, and secure SDLC processes. While implementing them can be challenging, especially for organizations with limited resources, you’ll find detailed information about each framework and its specific requirements as you scroll down this page.
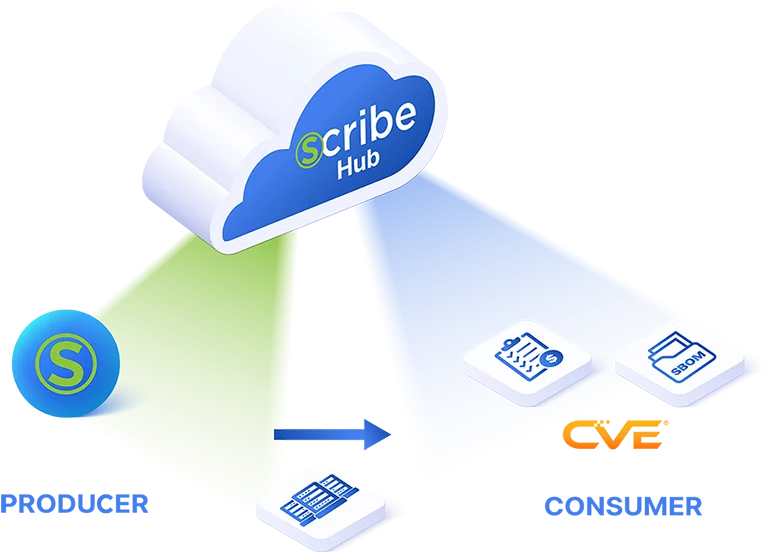
Scribe’s platform serves as a safe harbor to software producers. It enables easy compliance with SLSA and SSDF frameworks, even with limited resources
Scribe enables customers to comply with the SSDF framework and SLSA by promoting transparency through an evidence-based hub that ensures the software hasn’t been tampered with.
Get Solution Brief
Comply with NIST SP 800-218 (SSDF)
The SSDF aims to reduce the volume and impact of vulnerabilities that occur across the entire SDLC. Vendors operating or planning to operate in the U.S. must react quickly and learn how to comply with the SSDF.
The SSDF is not a checklist you should follow but rather a roadmap for planning and implementing a risk-based approach to secure software development. This includes promoting transparency and using an evidence-based strategy to protect software from any tampering by unauthorized users.
Scribe users can not only apply a policy over attestations to ensure secure development and build processes or to validate that tampering hasn’t taken place, but they can also gauge compliance with the SSDF—the basis for the new U.S. cyber regulation
Get the Complete SSDF Guide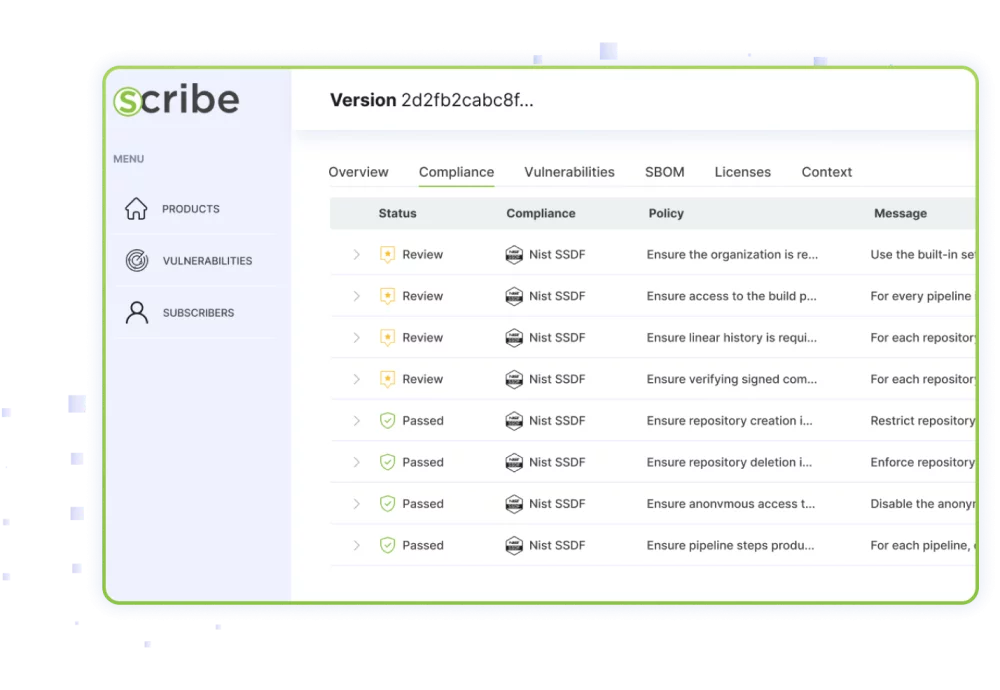
Scribe is the first solution to focus on the PS (Protect the Software) group of practices within the SSDF
Scribe conducts a rule-based evaluation to determine the protection level of the source code, based on the well-known CIS Software Supply Chain Security benchmark, combined with some elements from SLSA.
Read Use Case
Comply with the SLSA framework
SLSA is a comprehensive checklist of security controls and standards that ensure software integrity. In addition to helping developers, organizations, and businesses make informed choices about how to build and consume secure software, it proposes 4 escalating series of steps to securing the entire software development lifecycle.
Using Scribe, users can automate compliance validation with SLSA. On top of that, in the specific areas where they do not comply, Scribe provides a set of actionable recommendations to close the gap. This solves a huge problem for software producers who need to comply with the new U.S.-led regulation by 2024.
Read Use Case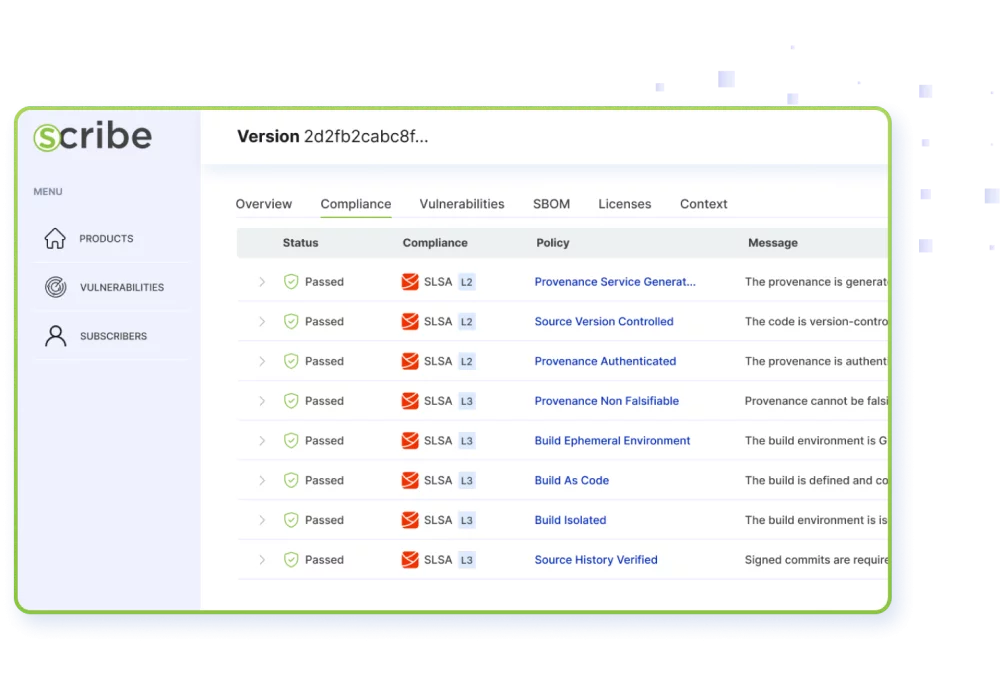
Easily verify that SW builds comply with SLSA level 2 or level 3 requirements
Scribe enables you to create SLSA provenance as part of each of your builds’ pipeline, see exactly which SLSA requirement has passed or failed, and quickly address any issues and bring the build into compliance.
You can then easily share the collected evidence with relevant stakeholders, confidently demonstrating your build or product compliance.

Achieve FedRAMP compliance faster, with fewer resources, while maintaining your development velocity
Scribe Security’s platform delivers critical features to streamline and automate compliance processes, ensuring faster time-to-certification with minimal manual effort:
- Automated SBOM Management
- Guardrails-as-Code for SDLC Governance
- Continuous Assurance: Code Signing and Provenance Verification
- Vulnerability Scanning and Risk Management
- Evidence-Based Compliance and Reporting
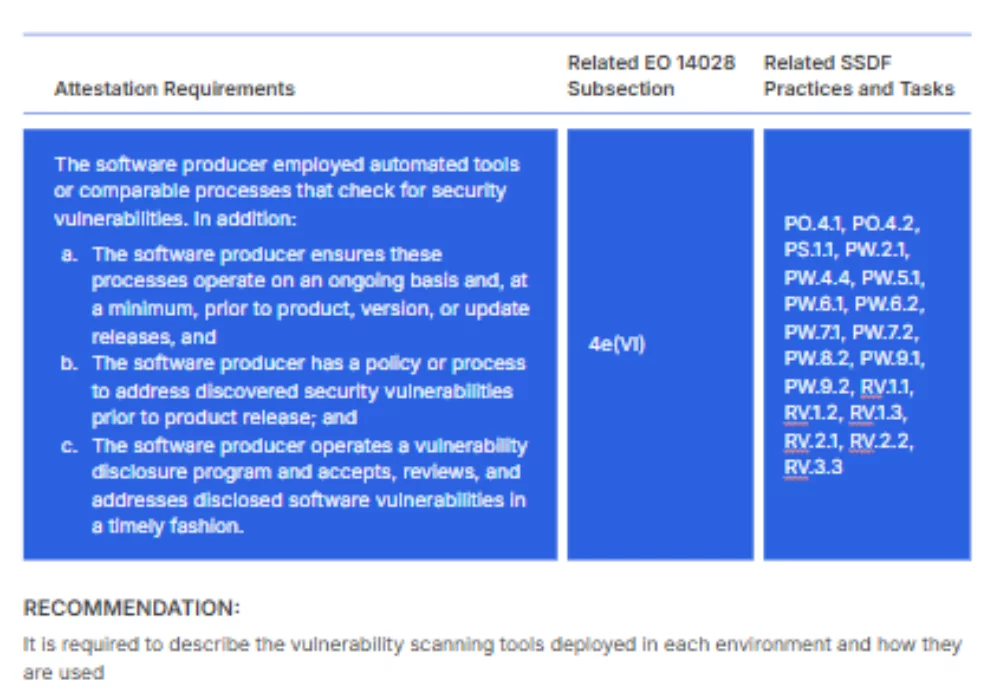
Navigating the requirements of CISA’s Secure Software Development-Attestation Form
We have your back:
- Scribe generates evidence, cryptographically signs that evidence into an attestation, and verifies that evidence as part of whatever policy is needed to enforce on software production process
- We advise on what should be part of the required evidence, including log files, screenshots, configuration files, and so on.
- We know how to collect evidence from 3rd party tools and include it with the rest of the evidence for SDLC and build pipelines.
- We help take this evidence and turn it into irrefutable, immutable attestations that are saved in a secure store.
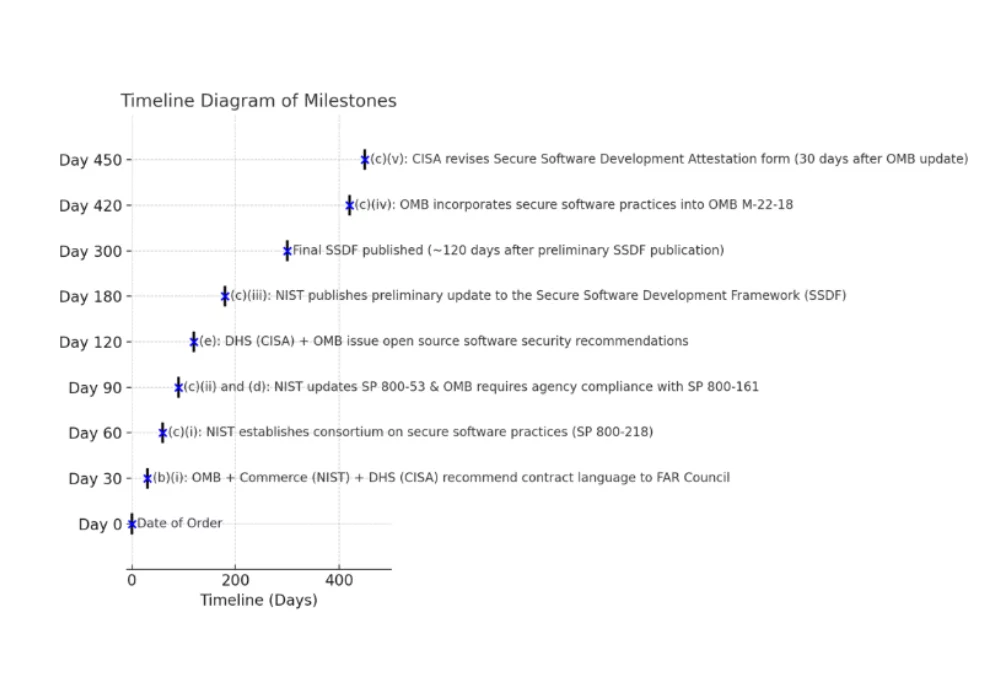
Meeting the New Federal Software Security EO 14144
Scribe’s attestation-based platform ensures full software supply chain security compliance with the new federal mandate. Scribe’s key advantage is its continuous assurance model, which includes:
- Seamless integration into CI/CD workflows (on-premise or cloud).
- Real-time security checks, including vulnerability scanning, license compliance, and policy enforcement.
- Immutable, signed evidence for every verification step, forming a secure chain of attestations.
- Automated policy enforcement to block non-compliant builds, preventing deployment of risky software.
Comply With DORA - Empowering Digital Operational Resilience in Financial Services
Scribe Security offers a holistic solution by automating security controls throughout the SDLC, ensuring that every release meets rigorous security standards, and providing verifiable, machine-readable evidence of compliance.
Scribe Security helps organizations in the financial sector not only comply with DORA but also build a resilient, secure software foundation.
Get the Complete White Paper Now
Empowering Cybersecurity Compliance for Medical Device Manufacturers
The FDA’s Cybersecurity in Medical Devices Guidelines outline stringent requirements for risk management, secure software development, and ongoing vigilance throughout a device’s lifecycle.
Scribe Security’s platform generates SBOM and manages the associated risk throughout the SDLC, embeds security directly into the SDLC, automates continuous attestations, and generates verifiable evidence—providing medical device manufacturers with the tools they need to meet FDA requirements and safeguard their products.
Get the Complete White Paper Now
Empowering Software Producers to Meet the EU Cyber Resilience Act
The EU Cyber Resilience Act (EU CRA) establishes comprehensive cybersecurity requirements for digital products, mandating that software producers adopt secure-by-design practices and maintain rigorous supply chain security.
Scribe Security’s holistic platform automates and enforces security across the entire Software Development Lifecycle (SDLC), ensuring that software is developed, released, and maintained in accordance with the EU CRA.
Get the Complete White Paper NowScribe’s Advantage Over Other Tools
Evaluates the entire policy rather than just producing a provenance document
Producers can collect relevant SLSA information about their pipelines, in the form of a series of policies
Producers can choose to enact these policies on their pipeline and check whether the policy has passed or failed
All policies passing means you are conforming to SLSA level 3.
The SSDF and SLSA frameworks cover a wide range of areas, including vulnerability management, code integrity, provenance validation, and enforcement of secure SDLC processes. However, implementing them can be a daunting task, particularly for organizations that have limited resources. Furthermore, the need to demonstrate compliance in an unequivocal manner in response to the new federal regulation or customers’ requirements is far from trivial.
With Scribe, You Can:
Generate, Manage, and Share SBOMs
Scribe allows commercial software vendors and integrators to track vulnerabilities, generate, manage, and share SBOMs with downstream consumers and other stakeholders in the software supply chain.
Manage SBOM Access
Scribe allows contractual obligations to permit access to SBOMs. It also communicates vulnerability risk through VEX (a CISA standard).
Determine the Protection Level
Based on CIS Software Supply Chain Security benchmarking and some elements from SLSA, Scribe conducts a rule-based evaluation to determine the protection level of the build pipeline.



