What is the XZ Utils (CVE-2024-3094) Backdoor?
CVE-2024-3094, published at the beginning of April 2024, is a backdoor maliciously inserted into a Linux utility. It was detected by Andres Freund, a curious and security-aware Microsoft software engineer, on the verge of being integrated into main Linux distributions. Had this succeeded, an unimaginable number of servers could be under the full control of malicious actors.
Details about this backdoor can be easily found; a news-level report by the Guardian, and technical analysis by Akamai, alongside the original alert-mail by Andres Freund are a few examples.
Responding to CVE-2024-3094 using SBOMs and ScribeHub
Organizations that manage their SBOMs with SBOM management tools can swiftly respond to this and similar backdoors and vulnerabilities; I will elaborate on responding using ScribeHub, Scribe’s software risk management platform that includes advanced SBOM management capabilities, by answering a few questions that you or your manager are probably asking yourself.
Step 1: Which of my systems are vulnerable?
- Scribe alerts on new critical and high vulnerabilities. If your systems’ SBOMs were generated and uploaded to ScribeHub, you would get a push notification alert to your mailbox about the products that are susceptible to the new vulnerability.
- Scribe enables you to search for specific packages across your product portfolio. With ScribeHub, you can search for this package directly. Here is a snapshot of how it would appear on the ScribeHub Dashboard:
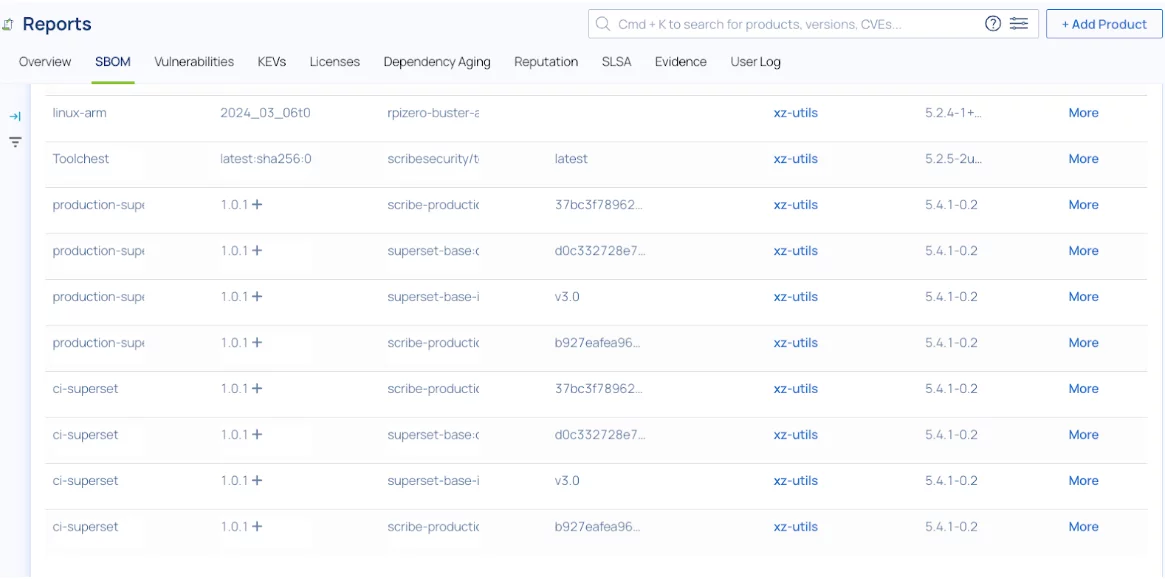
- This view enables you to immediately understand which products are vulnerable. You can use this information to prioritize actions (for example, assigning high priority to the Payments application and low priority to the Internal-Lunch-Orders application).
Step 2: How do I ensure a vulnerable container does not enter my production systems?
It is difficult to deploy SBOM generation in a large software development organization; there are many projects, many urgent tasks, and urgent needs to integrate third-party containers.
Scribe’s Kubernetes admission controller acts as the gatekeeper of the operational clusters. The Scribe policy engine enables you to deploy a policy with three simple rules:
- Alert or block deployment of images without an SBOM. This rule ensures that you will have response capabilities to such events from now on.
- Block the deployment of images using xz-utils versions 5.6.0 or 5.6.1. This rule ensures that vulnerable containers are not created in your cluster.
- Block deployment of images that have vulnerabilities with CWE-506 (the weakness tag of a backdoor). This rule is about “learning your lesson” – block any image that has a vulnerability that NVD marked as malicious code.
Step 3: How do I ensure no images with this vulnerability are hiding around my systems?
Images may have already been deployed or pushed to image registries. Scribe Scanner enables you to gain visibility into all your images. Set up a scanning task and get immediate visibility into all the images in your image registry and your Kubernetes clusters. After scanning, all your images will have their SBOM stored at ScribeHub; you will get a critical vulnerability alert and gain the capability to search these SBOMs. In addition, you can run a policy evaluation on all your images.
Step 4: How do I reduce the risk of the next XZ case?
One way to reduce such a risk is to decide not to be a first adopter of new versions of software packages, especially if the old versions are not vulnerable. Scribe enables you to achieve this in two ways:
- Using ScribeHub BI capabilities, you can get a report of packages that have been upgraded between product versions.
- ScribeHub enables you to set a policy to block or alert on the use of such software versions.
Interested in hearing more about ScribeHub’s amazing capabilities? Contact us
This content is brought to you by Scribe Security, a leading end-to-end software supply chain security solution provider – delivering state-of-the-art security to code artifacts and code development and delivery processes throughout the software supply chains. Learn more.



