The risks faced by software supply chains have taken their place at the forefront of conversations in the cybersecurity ecosystem. This is partly due to the increased frequency of these supply chain attacks, but also because of the potentially far-reaching impacts they have when they do happen.
Figures from 2021 showed software supply chain attacks tripled in frequency from the previous year, a trend that is unlikely to slow down in the future. Fortunately, the growing awareness of the risk of software supply chain attacks is prompting a wide range of potentially beneficial actions. One such recent action is the issuance of an Executive Order on Cybersecurity by the United States government.
What’s even more reassuring is the growing interest of many of the big players in collectively introducing measures that can aid in the fight against the growing threat of malicious actors targeting software supply chains. In October 2022, Google announced a new open-source project known as Graph for Understanding Artifact Composition (GUAC, for short). Although this initiative is still in its early stages, we find it quite interesting because it holds the potential to change the industry’s current understanding of software supply chains and introduces advanced measures to further mitigate these threats.
Why GUAC? Why Now?
As an organization, Google’s core mission is to organize the world’s information and make it universally accessible and useful. The Graph for Understanding Artifact Composition (GUAC) is in line with that mission as far as the cybersecurity world is concerned. The goal of GUAC is to make top-level security information available for all organizations, including those who do not have the IT budget or enterprise-scale security infrastructure to get this information for themselves.
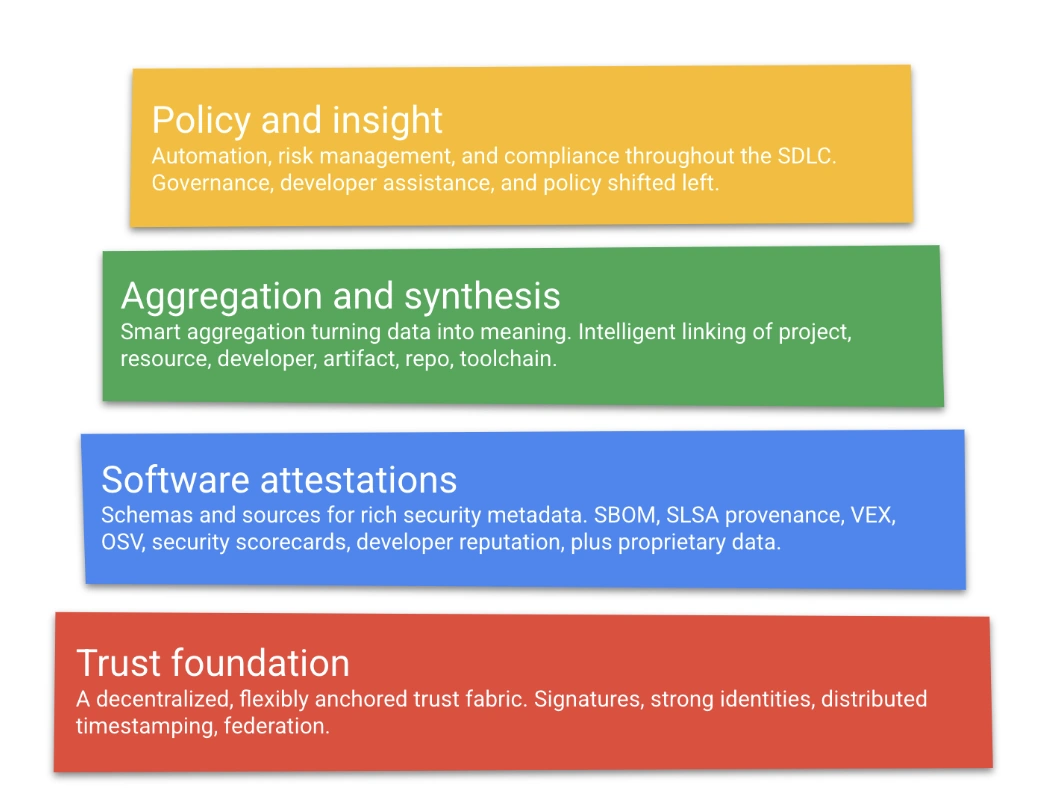
GUAC is an attempt to aggregate valuable software security metadata into a high-fidelity graph database. The database will not only include the identity of different software entities but will also detail the standard relationship between them.
Community collaboration between various groups has led to policy documentations like the Software Bills of Materials (SBOMs), signed attestations that detail how software is built (such as SLSA), and databases that make it easier to discover and eliminate vulnerabilities, like the Global Security Database (GSD). GUAC will help combine and synthesize the information available on all these databases and organize them into a more comprehensive format. This way, anyone can find the answers they need to high-level security questions about any software assets they intend to use.
GUAC covers three stages of software supply chain security
GUAC is a free open-source platform that will aggregate the different sources of software security metadata into a single source. As a security tool, GUAC will be useful to organizations in the three stages of securing their software infrastructure against supply chain attacks. Here’s how it’ll be useful for each of these stages:
Stage #1: Proactive
The proactive stage is where you put measures in place to prevent large-scale software compromises from happening at all. At this stage, you’ll want to know the critical components of your software supply chain ecosystem that you use most, and GUAC will make it easier to identify them. With GUAC, you can identify weak points in your overall security infrastructure, including areas where you’re exposed to risky dependencies. This way, you’re better positioned to forestall attacks before they happen.
Stage #2: Operational
The operational stage is the preventive stage where you determine if the software you want to use or deploy checks all the right boxes as far as safeguards against supply chain risks are concerned. With GUAC you can verify if the software meets the required policy stands or if all the binaries in production can be traced back to a secure repository.
Stage #3: Reactive
Despite all measures, a supply chain breach may still occur. The reactive stage is where you determine what to do when a breach is discovered. With GUAC, affected organizations can find out which part of their inventory has been affected by the vulnerability, how badly they’re affected, and what the risks are. This information will help mitigate an attack and prevent a recurrence in the future.
What does GUAC mean for you?
So what does GUAC mean for you as an organization or cybersecurity professional? As the project is still in its development stage, there are various ways you can get involved either on an individual level or as an organization.
- For starters, it’s a call to get involved. Statistics from a survey of about 1,000 CIOs show that up to 82% of those interviewed believe their organization is vulnerable to cyberattacks. This means that if you’re not putting any measures in place to secure your software infrastructure, you should be doing so now more than ever. This move by Google is another wake-up call on the need to take more action towards taking software supply chain security more seriously.
- Second, this is a call to contribute. GUAC is currently an open-source project on Github. All it is now is a proof of concept that aggregates SLSA, SBOM, and Scorecard documents to support the simple search for software metadata. The project welcomes contributors to add metadata to GUAC as well as advisors that represent the needs of end users.
- GUAC is a great new pairing for the SLSA framework. The security framework— a collaboration between various cybersecurity stakeholders—is a set of agreed-upon industry standards that businesses and individual developers can adopt to make informed security decisions when building software. Combined, these two policy documents will help drive better outcomes as far as software security is concerned.
- GUAC also attests to the growing importance of the Software Bill of Materials (SBOM). This formal list of all the artifacts used in software decreases the risks of security vulnerabilities for users and also helps them know how to act and where to look for vulnerabilities when breaches occur.
- Finally, you should know that the only way to guarantee the integrity of all third-party components of your software is to make sure every code that you did not write yourself is fully accounted for, untampered with, and free of all malicious code. Fortunately, there are software supply chain security tools and frameworks that can help you monitor every component across your entire Software Development Lifecycle (SDLC). Here’s an article that can be a good starting point to help you find the right software supply chain security tool for your own needs.
This content is brought to you by Scribe Security, a leading end-to-end software supply chain security solution provider – delivering state-of-the-art security to code artifacts and code development and delivery processes throughout the software supply chains. Learn more.