In an era where cyber threats are growing in both sophistication and scale, organizations are increasingly relying on artificial intelligence (AI) to strengthen their security frameworks. This trend is particularly significant in software supply chain security, where AI is becoming a crucial tool in identifying vulnerabilities, predicting emerging threats, and streamlining the development and deployment of secure software.
As attacks targeting software supply chains, such as the infamous SolarWinds and 3CX breaches, become more frequent and impactful, the adoption of AI-driven security tools has emerged as a vital strategy. This article explores the role of AI in enhancing software supply chain security and how it is transforming the way organizations safeguard their digital assets.
AI’s Role in Identifying Vulnerabilities
At the core of AI’s value to software supply chain security is its ability to automatically identify vulnerabilities across vast and complex codebases. Traditional vulnerability identification often relies on manual reviews or static analysis tools, which can miss critical security flaws or generate overwhelming numbers of false positives. AI, however, offers a more dynamic approach by:
- Automating the Detection Process: AI can autonomously scan and analyze both open-source and proprietary code to uncover vulnerabilities, misconfigurations, and potential security risks. This process is not limited to merely detecting known vulnerabilities (CVEs) but can also identify unknown or emerging threats by analyzing patterns in code behavior.
- Real-Time Vulnerability Management: One of AI’s greatest strengths is its ability to work in real-time. By integrating AI tools directly into CI/CD pipelines, security vulnerabilities are detected as soon as new code is committed. This significantly shortens the window between vulnerability identification and remediation, making software development faster and safer.
- Prioritization: AI-driven tools can intelligently prioritize vulnerabilities based on factors such as exploitability, severity, and the potential business impact. This allows security teams to focus on addressing the most critical issues first, reducing the likelihood of high-risk vulnerabilities being exploited.
By integrating AI, organizations can efficiently scan for vulnerabilities that traditional methods might overlook, significantly reducing the risk of supply chain
Threat Prediction and Proactive Security
In addition to identifying vulnerabilities, AI’s ability to predict emerging threats is transforming how organizations approach cybersecurity. Instead of reacting to security incidents after they occur, AI models can analyze historical data, recognize patterns, and predict future threats, enabling proactive defense.
- Threat Intelligence and Prediction: AI can analyze vast amounts of threat intelligence data—ranging from malware signatures to known attack vectors—and detect patterns indicative of future attacks. By correlating data from various sources, AI can predict the likelihood of certain attack types targeting specific aspects of the software supply chain. This predictive capability helps organizations deploy defenses before an attack takes place, reducing the chance of a successful breach.
- Behavioral Analysis: AI can also be used to detect anomalies and unusual behavior in software systems that could indicate a potential attack or compromise. This is especially useful in identifying supply chain threats, where malicious actors often seek to implant vulnerabilities in trusted software components. AI tools can continuously monitor for deviations from established behavioral norms, flagging suspicious activity early in the process.
- Zero-Day Threat Detection: AI’s ability to spot patterns that may signify an emerging zero-day vulnerability is another powerful feature. While traditional security measures may miss these entirely, AI can analyze the flow of data and behavior within a system, predicting how an undiscovered vulnerability might be exploited.
By utilizing AI’s predictive capabilities, organizations can shift from a reactive security posture to a proactive one, significantly improving their ability to fend off attacks before they reach critical systems.
Enhancing the Software Development Lifecycle (SDLC)
AI is revolutionizing the Software Development Lifecycle (SDLC) by embedding security at every stage—from development to deployment. By incorporating AI-driven security measures into the SDLC, organizations can ensure that software is secure by design, rather than bolting security onto the finished product.
- Secure Code Development: AI tools can assist developers by providing real-time feedback on security issues as they write code. This not only improves the overall security of the software but also reduces the need for lengthy code reviews and security patches later in the development process. AI-powered assistants can highlight coding mistakes, suggest security best practices, and flag any suspicious patterns in real-time, ensuring that security is embedded early in the SDLC.
- Automated Testing: AI is also making significant strides in automated security testing. Rather than relying on traditional, time-consuming manual testing methods, AI-powered tools can run automated security tests at various stages of the development cycle. These tests simulate attacks and analyze the software’s response, identifying vulnerabilities that could be exploited by attackers. By automating this process, organizations can perform comprehensive security testing on a continuous basis, ensuring that software is always secure, even as new updates are rolled out.
- DevSecOps Integration: AI can play a key role in DevSecOps (Development, Security, and Operations) by ensuring that security measures are not only integrated into the development pipeline but also continuously monitored and adjusted as needed. AI-driven security tools can seamlessly integrate with existing DevOps workflows, ensuring that security is an ongoing, automated process rather than an afterthought.
Benefits of AI in Software Supply Chain Security
The application of AI to software supply chain security offers numerous benefits, including:
- Speed and Efficiency: AI can process and analyze vast amounts of data far more quickly than human teams, allowing for rapid identification and remediation of security issues.
- Reduced Human Error: By automating many aspects of security, AI reduces the likelihood of human error, which can be a major factor in cybersecurity incidents.
- Scalability: As software supply chains grow increasingly complex, AI provides the scalability needed to manage security across large, distributed systems.
- Real-Time Insights: AI offers real-time insights into security vulnerabilities, making it possible to address issues before they become critical.
Heyman, Scribe Security’s Slack AI-Based Chatbot: Revolutionizing Software Supply Chain Security, AppSec, and DevSecOps
In today’s fast-paced digital environment, cybersecurity is no longer just a priority—it’s an absolute necessity. As organizations accelerate their software development cycles through continuous integration and delivery (CI/CD), the need for robust security measures across the software supply chain has become increasingly important. One of the biggest challenges organizations face is integrating security into these processes without disrupting productivity. Enter Heyman, an AI-powered chatbot developed by Scribe Security, which aims to streamline security operations by identifying vulnerabilities, automating remediation, and providing continuous compliance assurance.
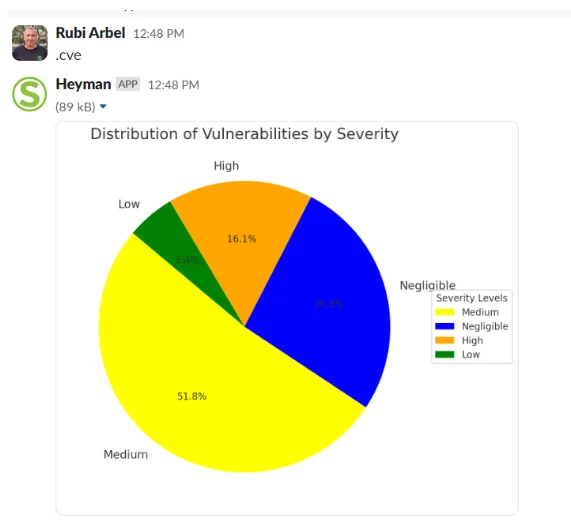
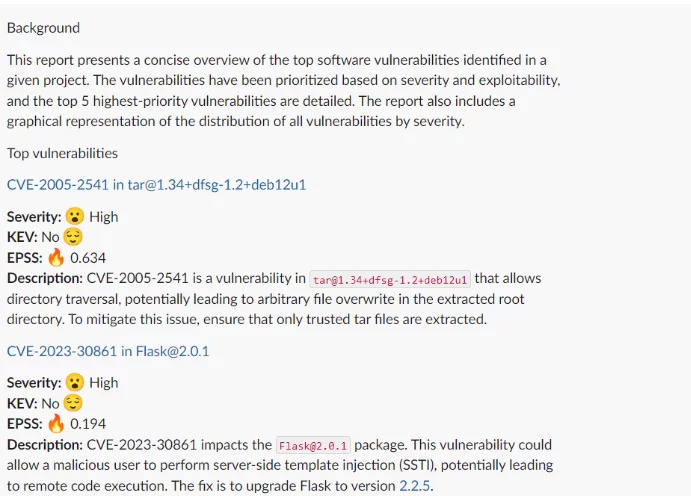
1. Proactive Vulnerability Detection and Prioritization
Heyman’s most significant capability is its ability to proactively identify and prioritize vulnerabilities across an organization’s software supply chain. In the modern world of continuous software development, vulnerabilities can appear at any stage—from open-source components to proprietary code. Heyman’s advanced AI capabilities allow it to automatically detect these vulnerabilities, helping security teams pinpoint critical security gaps before they can be exploited.
Using AI-powered algorithms, Heyman assesses the severity and exploitability of vulnerabilities and provides a ranked list of priorities. This ensures that development teams can focus on addressing the most pressing issues first. By automating vulnerability detection and triaging, Heyman helps reduce the risk of breaches and makes security a seamless part of the development process.
2. Streamlined Remediation and Task Management
In addition to identifying vulnerabilities, Heyman helps streamline the remediation process. Through its integration with popular project management and issue tracking platforms like Jira, Heyman can automatically create and track remediation tasks. This means that as soon as a vulnerability is identified, it can be logged, assigned to the appropriate team, and tracked to completion, ensuring that no critical security issues are overlooked.
Heyman’s ability to automate this process removes much of the manual overhead typically associated with vulnerability management. This not only accelerates remediation but also ensures that security issues are promptly addressed without falling through the cracks.
3. Enhancing Security Posture Through Continuous Monitoring
Security is not a one-time process; it requires ongoing vigilance and attention. One of Heyman’s most valuable features is its capability for continuous monitoring of security posture. By continuously analyzing the software environment, Heyman identifies potential security gaps as they arise, helping to maintain a secure state at all times.
Heyman continuously scans code repositories, configurations, access controls, and dependencies to detect issues such as misconfigurations, outdated libraries, and unpatched vulnerabilities. This real-time monitoring allows security teams to address issues as soon as they emerge, rather than relying on periodic audits or scans. By maintaining constant oversight, Heyman ensures that organizations stay ahead of threats and maintain a strong security posture throughout the software development lifecycle.
4. Automation in Compliance and Continuous Assurance
As organizations adopt more complex and distributed software supply chains, regulatory compliance becomes increasingly critical. Frameworks such as the Cybersecurity and Infrastructure Security Agency (CISA) guidelines, the NIST Secure Software Development Framework (SSDF), and SBOM (Software Bill of Materials) sharing requirements demand robust and verifiable security practices.
Heyman excels in ensuring compliance by automating evidence collection and providing real-time validation of security controls. Instead of relying on manual audits or periodic reviews, Heyman delivers continuous compliance assurance by generating automated reports and alerts based on real-time security events. This not only saves time but also reduces the likelihood of non-compliance with security regulations.
Heyman ensures that organizations maintain a fact-based, evidence-driven approach to security compliance. By automating the generation and analysis of security attestations, Heyman helps organizations prove that they are meeting regulatory requirements, minimizing the risk of fines or penalties related to non-compliance.
5. Prioritizing and Mitigating Security Threats
One of the most significant challenges in DevSecOps environments is determining which security issues to address first, especially when faced with an overwhelming number of vulnerabilities and configuration issues. Heyman alleviates this challenge by using AI-driven insights to prioritize the most critical threats.
By analyzing vulnerabilities based on factors such as exploitability and severity, Heyman provides actionable recommendations to the security team, guiding them on which issues require immediate attention. This prioritization ensures that the most significant threats are mitigated first, allowing organizations to make the best use of their resources and minimize security risks efficiently.
Additionally, Heyman supports automated remediation suggestions, giving security teams clear, actionable steps on how to fix vulnerabilities, apply patches, or update misconfigurations. This intelligent prioritization and guidance make it easier for teams to stay focused on what’s most important, without getting bogged down by low-priority issues.
6. Enabling DevSecOps with Real-Time Feedback
Integrating security into the DevSecOps pipeline is often challenging due to the need for real-time feedback that doesn’t slow down the development process. Heyman addresses this by providing instant feedback to developers and security engineers throughout the development lifecycle.
As code is committed and pushed through CI/CD pipelines, Heyman analyzes the generated security evidence and the attestations collected for vulnerabilities, configuration issues, and compliance risks. The results are provided to the relevant teams upon request in a conversational manner, allowing them to address any security issues. This feedback enables teams to remediate security issues quickly and efficiently without disrupting the flow of development.
Moreover, Heyman’s integration into platforms like Slack ensures that security feedback and alerts are easily accessible to all team members. By embedding itself within the existing communication and collaboration tools that teams use, Heyman becomes a seamless part of daily operations, reducing friction between security and development teams.
7. Supporting a Strong Security Governance Framework
As organizations increasingly adopt Zero Trust models and rely on continuous security assurance, Heyman provides critical support for evidence-based governance. Rather than relying on traditional trust-based relationships with third-party vendors or internal teams, Heyman helps organizations build security governance based on verifiable, continuous evidence.
Through its automation of attestation generation, continuous monitoring of code and configurations, and collection of security evidence, Heyman provides a robust framework for security governance. This helps organizations demonstrate accountability and transparency, both internally and to external stakeholders such as customers, regulators, and auditors.
Heyman’s ability to gather, analyze, and validate security data in real-time means that organizations can quickly respond to inquiries about their security posture and demonstrate compliance with regulatory requirements. This helps build trust with stakeholders and improves the organization’s overall security culture.
Conclusion
Heyman, Scribe Security’s AI-powered chatbot, is transforming the way organizations manage software supply chain security, AppSec, and DevSecOps. By assisting with identifying and prioritizing vulnerabilities, automating remediation, providing continuous compliance assurance, and delivering real-time feedback, Heyman helps organizations maintain a secure development pipeline while meeting regulatory requirements.
As cyber threats continue to evolve, having a tool like Heyman integrated into Slack and analyzing attestations collected from your security operations ensures that you stay ahead of vulnerabilities, enhance your security posture, and comply with the latest standards. With Heyman’s assistance, organizations can build a more secure, resilient, and compliant software development environment—without sacrificing speed or efficiency.
This content is brought to you by Scribe Security, a leading end-to-end software supply chain security solution provider – delivering state-of-the-art security to code artifacts and code development and delivery processes throughout the software supply chains. Learn more.



