We’ve all heard a lot about SBOMs recently. We heard about their usefulness, their composition, and their requirements for security and regulation. This time I want to take the time to talk about a little less-known segment of the CyclonDX SBOM – the Dependency Graph.
Unlike the name implies the Dependency Graph is not a visual aspect of the SBOM. Its purpose is to help describe components’ dependency on other components. This relies on a components’ bom-ref – a unique identifier for each SBOM component. The idea is to show what elements are dependent on or connected to each other. Sounds simple enough, right?
Scribe uses the Dependency Graph a lot in the process of deciding what elements of the SBOM are important and what we should pay attention to. In this article, we’ll look into the way Scribe uses the SBOM Dependency Graph and the practical benefits we can reap from it. We’ll look at some JSON examples of an SBOM Dependency Graph and conclude with a look at what else we can do with it in the future.
What Is the Dependency Graph?
The Dependency Graph was added to the CyclonDX format in 2019. Its declared purpose was to tie components together using a unique identifier that later came to be known as a bom-ref. In the CycloneDX use-cases example, we can see how the dependencies use the components reference ID to show what is dependent on what:
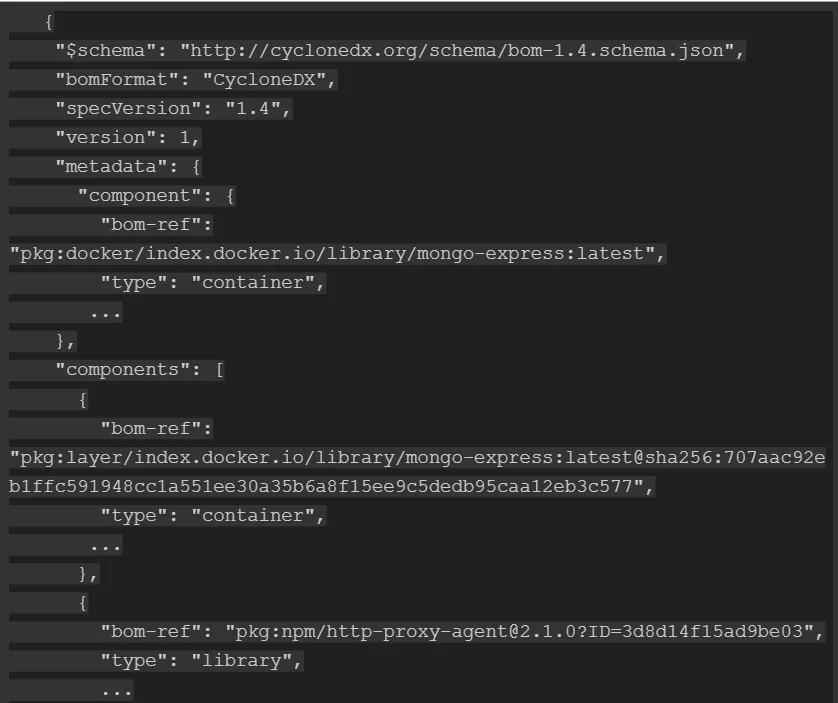
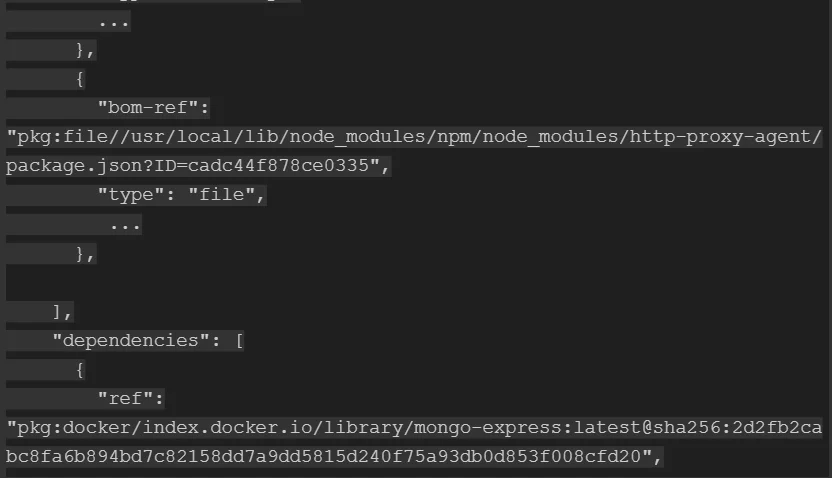
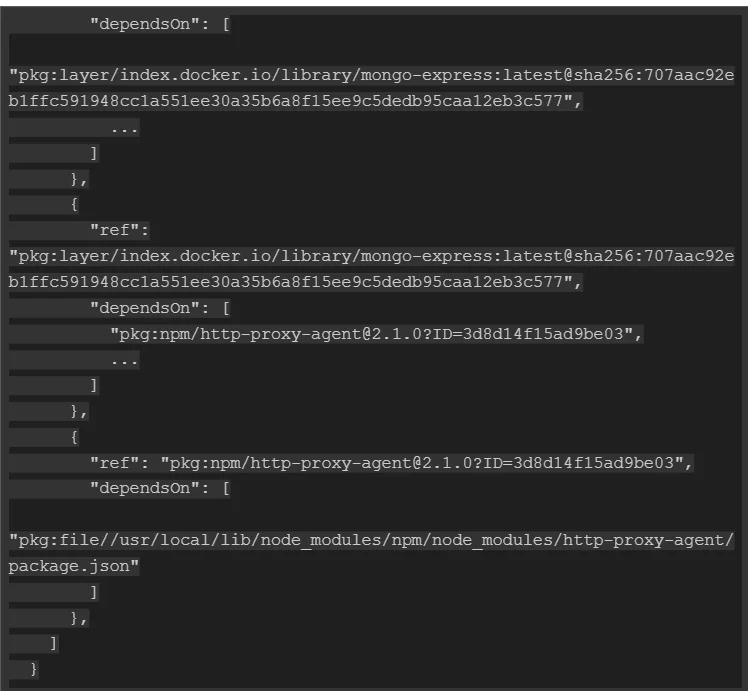
Even without going into examples, I’m sure you can see that the ability to connect one element to others can be useful. For one thing, as the most common use case, it allows you to immediately see all of a library’s dependencies in a single place.
A dependency graph can represent both direct and transitive relationships and is typically one node deep.
Although a complete dependency tree is capable of being represented, it is not recommended because it could result in endless loops due to circular dependencies or other complex relationships. It’s advised to keep your graphs simple by representing a single node.
How Is Scribe Using the Dependency Graph?
Scribe makes extensive use of metadata collected along with the SBOM to give the evidence context. The evidence’s context includes where and when it was collected, what’s its subject, and so on. As Scribe strives to offer reliable, reusable information, we make use of the dependency graph to create connections that can be used across different clients and projects.
Here are the dependency graph links that Scribe supports:
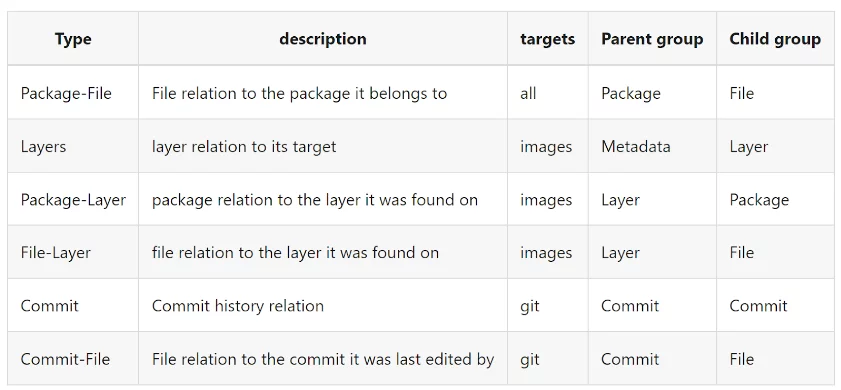
Source: Scribe Documentation
- Package-File: This connection allows us to see which files belong to each package. Obviously, if we find a file in a package where it doesn’t belong it’s a clear indication of a problem.
- Layer indication and Package-layer: Knowing what packages are located in what image layer is handy since that way we can order the vulnerabilities by layers. Problems that you have inherited from your base image or your parent image would not have the same urgency and your direct ability to influence them as ones that are found on layers you’ve created yourself.
- Layer-File: Similar to the package-file connection this connection allows us to see what files are associated with each layer. In tandem with the other connections, we can verify that files are associated with the right package and layer and that there are no files in places where they shouldn’t be.
- Commit and Commit-File: By identifying which files came from which commit we can make sure that there were no undue changes in the commit files before they were used to build the final image.
Using all this information together we can draw a pretty comprehensive image from the SBOM about what files should be found where. As a result, we have a better chance to catch outliers or aberrations that might indicate a problem in your image – either an integrity problem or a potential attack.
Dependency Graph and Policy Enforcement
Scribe leverages this comprehensive dependency graph to enforce intricate policies effectively. For instance, the Commit-File dependency is harnessed to uphold code owner policies. It enables us to verify who committed which file and when. The Package-File dependency is employed to ensure package integrity policies. It allows us to check which files are supposed to be linked to each package and to verify that this is indeed the case. Additionally, the Package-layer dependency is used to tailor package policies to the specific requirements of each layer. Since each software image may construct its layers differently it’s invaluable to be able to know definitively which packages are linked to which layer of the image.
Customizing Your Dependency Graph Information
We know that not everyone is keen to share all this information or that they do not care to see it or use it in any way.
As a way to address that, Scribe allows you to create more specific versions of your SBOM. Here are the customization options you can use with our Valint tool while creating SBOMs that we’re currently supporting. Additional options are going to be available in the future:
- To include only specific component groups, use –components to select between the group types.
- To include or exclude specific package types, use –package-type or –package-exclude-type to select a specific package type.
- To include the installed packages found (package group install) or the packages referenced by sources (package group index), use –package-group to select between options.
- To exclude components, use –filter-regex, –filter-scope, and –filter-purl to exclude any component you want to be excluded.
- To attach any file content, use –attach-regex to include the content of external files.
- To include custom environments and labels, use –env and –label to attach your custom fields. This allows you to add custom metadata to the SBOM you’re creating.
Looking to the Future
Scribe considers the context and the connections we make between the different components of your SBOM using it of the utmost importance. With our Valint’s ability to sign, verify, and manage policies we consider it totally possible to see a future where more can be done than just manage security policies. We can imagine a future where the dependency graph information can be used in quality control, specific compliance needs, and even unrelated fields like fintech and agriculture.
Scribe’s platform has a free tier where you can start trying it now with all the capabilities at your fingertips to play with. I encourage you to give it a try, see the usefulness of such information accumulated over time, and see what you can use the information for. I hope you’ll join us as we welcome a more secure future for all of us.
This content is brought to you by Scribe Security, a leading end-to-end software supply chain security solution provider – delivering state-of-the-art security to code artifacts and code development and delivery processes throughout the software supply chains. Learn more.



