The traditional approach to securing software products focuses on eliminating vulnerabilities in custom code and safeguarding applications against known risks in third-party dependencies. However, this method is inadequate and fails to address the full scope of threats posed by the software supply chain. Neglecting to secure every aspect of this chain, from production to distribution and deployment, exposes organizations to attacks such as malware, data breaches, and intellectual property theft. Ignoring this critical step is a serious disregard for the organization’s security.
In this article, we will examine the rising trend of cyber attacks directed at the software supply chain, as well as recent regulatory advancements and best practice frameworks that have arisen in response to this growing danger. We will also shed light on the need for a fresh strategy to secure your software supply chain, one that surpasses current application security measures. We will illustrate why current investments in application security offer some protection, but do not completely mitigate your cyber security risks in this area. Finally, we will outline what is necessary to complement them for full protection.
For the complete White Paper click here >>>
Why securing the software supply chain is important
The use of third-party tools, libraries, and open-source software in software development increases both the complexity of the software supply chain and the risk of potential vulnerabilities and attacks. Attackers can target a specific link in the supply chain to gain access to sensitive information or disrupt operations. These attacks can have a significant impact on organizations and their supply chain partners.
The fallout from several software supply chain attacks has made headline news in recent years. As a consequence, Gartner has predicted recently that by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains, a three-fold increase from 2021.
As software supply chain security gains attention, various application security solution vendors are rebranding themselves as offering solutions in this space. But is software supply chain security simply a new term for traditional application security, or is it a distinct market segment with unique characteristics and technologies? Is having an application security (AppSec) program in place sufficient to address software supply chain security, or do organizations need to adopt separate standards and technologies to ensure the security of their software and its supply chain? This question will be explored further in the article.
Emerging regulation and best practices frameworks
The U.S. Executive Order on Cybersecurity and other similar regulations reflect the growing importance of software supply chain security and the need for organizations to take appropriate measures to protect their software and its supply chain. The increasing interest shown by major players in collectively introducing measures to combat the threat is a positive development and indicates a growing recognition of the need for a coordinated and industry-wide approach to address the growing threat.
Some of the key initiatives to address software supply chain security include: Enhancing software development practices; improving supply chain visibility; implementing secure software procurement practices; and developing threat intelligence capabilities. Overall, these initiatives aim to increase the security of software and the supply chain by reducing the risk of attacks and ensuring that software is free from vulnerabilities and malicious code.
Below is a brief overview of the key initiatives:
- NIST’s SP 800-21 Secure Software Development Framework (SSDF) aims to boost software supply chain security for U.S., government suppliers. It offers secure development practices for organizations’ SDLC to minimize vulnerabilities and future threats. The guidelines are customizable and sector-agnostic. Read this whitepaper for more on the SSDF’s impact on the software industry.
- The United States Office of Management and Budget (OMB) released, in 2022, two memos on software supply chain security and the role of SBOMs in ensuring the security and integrity of the software supply chain. Organizations must comply by 2024 and ensure the security of their software and its supply chain. Federal agencies must implement guidelines, including sharing information and obtaining artifacts from vendors.
- The Supply Chain Levels for Software Artifacts (SLSA) Framework is a comprehensive set of security controls and standards designed to ensure the integrity of software supply chains. It was developed by OpenSSF, Google, and other cybersecurity stakeholders. By following this end-to-end framework, unauthorized changes to software packages can be prevented. Adopting SLSA can help protect against common supply chain attacks.
- The EU Cyber Resilience Act aims to improve the cyber resilience of organizations in the EU. It requires organizations to make SBOMs available for all software products they use in order to help them identify and address potential security vulnerabilities early on. The act also requires organizations to report vulnerabilities to ENISA/CERT-EU.
- The Center for Internet Security (CIS) developed the CIS Software Supply Chain Security Guide, which covers the phases of the software supply chain, from code contribution to delivery to end consumers. The guide provides best practices for securing the software supply chain, including establishing a security program, implementing secure development practices, conducting regular security assessments of suppliers, implementing security controls for distribution and deployment, and continuously monitoring for vulnerabilities and attacks.
- Sigstore is an open-source project focused on securing software supply chains. It provides a method for better-securing software supply chains in an open, transparent, and accessible way. The key to securing software supply chains is digitally signing the various artifacts of which applications are comprised. Sigstore aims to make software signing ubiquitous and easier by providing a simplified and quicker solution, compared to traditional digital signing solutions. The project also creates an open and immutable activity log.
The goal and tasks of the AppSec discipline
The AppSec team in mature software producer organizations focuses on securing software through developer training, code review, automatic scanning, and monitoring dependencies. The most common tools are static and dynamic application software testing (SAST and DAST) for testing applications, and software composition analysis (SCA) to detect known vulnerabilities in open-source dependencies.
To cope with the evolving threat landscape, several newer solutions have been devised and adopted. One such solution is the use of secret detection tools, which aid organizations in identifying secrets such as credentials, API keys, and sensitive data that may have been unintentionally disclosed in the code. Additionally, new scanning tools have been created to detect vulnerabilities in containers and infrastructure-as-code (IaC) in cloud computing environments, allowing organizations to ensure the security of their applications as they transition to the cloud.
To manage the vast array of security tools, orchestration solutions have arisen to provide a unified view of security across the SDLC. These solutions centralize the management of security tools and policies, streamlining the security process and reducing the risk of missed vulnerabilities.
Triaging, deduplication, and prioritization of security alerts are among the major challenges faced by AppSec owners. It can be overwhelming to manage the volume of alerts and to determine which ones require immediate attention and which can be disregarded. Additionally, AppSec owners need to assess the impact of the vulnerabilities on their specific systems, which requires a deep understanding of the technology stack and applications.
The AppSec approach covers the SDLC from code writing through build, packaging, and testing and is crucial in reducing vulnerabilities in both custom code and open-source components, thus mitigating liability for software producers and operators. Leading vendors in this space include Veracode, Checkmarx, Snyk, Synopsis, and Fossa.
The diagram below offers a simplified overview of the AppSec market, showcasing several key players.

A simplified view of the AppSec market landscape
While AppSec solutions can be effective in detecting known vulnerabilities and insecure code patterns, they tend to be reactive rather than proactive; they do not proactively reduce the attack surface. Moreover, the high volume of false-positive alerts generated by scanners can make it challenging for developers to focus on the most critical security issues. The scanning process can also be time-consuming and disruptive to the development timeline, adding friction to the development process and slowing down the release of new software.
The emerging role of software supply chain security
AppSec solutions overlook areas of the SDLC that may be vulnerable to attack and that affect the software supply chain. These areas include development tools, code repositories, source code management systems, build servers, and artifact registry systems, which may contain vulnerabilities and misconfigurations.
On the other hand, from the software consumers’ perspective, a common concern is that third-party software can introduce security vulnerabilities that are difficult to detect and mitigate. It’s important for consumers to thoroughly assess and vet the software they use, as well as regularly monitor and update it to reduce these risks.
To overcome these challenges, both software producers and consumers need to adopt a wider approach. Software producers should integrate into all stages of the SDLC and leverage automated tools to address security threats.
- CI/CD posture management – To secure the software supply chain, secure SDLC is crucial. CI/CD posture management automates discovery and enforces security practices. Visibility into SDLC and secure infrastructure use in development environments is a challenge for enterprises these days. CI/CD posture management must include server authentication, restrictions on public repos/buckets, and key expiration. Limiting risky development practices, such as executing unverified resources and referencing externally altered images, improves software security and reduces supply chain attack risk.
- Attestation and Provenance – Maintaining software supply chain security requires attestation (verifying software authenticity) and tracking provenance (origin, ownership, and custody). Attestation and provenance inform trust decisions, reducing risk of tampering, vulnerabilities, and inadequate security in development while ensuring industry standards compliance.
To effectively implement attestation and provenance, evidence from sources like source code managers, CI tools, build servers, etc. must be gathered and cryptographically signed. Evidence includes developer identity, code review proof, file/artifact hashes, and security posture of tools. Policies over attestations ensure secure development and build, tamper validation, and compliance with standards like SSDF and SLSA.
Existing APIs and observability solutions cannot collect evidence, sign attestations, and create provenance traces. New agents must be developed to trace data generated during SDLC and sign evidence for integrity and authenticity.
To the same end, beyond the SDLC, both software producers and consumers need to seek means to achieve the following:
- Continuous compliance – Continuous verification helps maintain compliance and protect against vulnerabilities even after deployment. This involves continuous monitoring and verifying the security of software components throughout the entire software development and deployment process. An SBOM is an important tool for continuous verification that lists software components and their versions used in a project. SBOMs facilitate vulnerability scans, help organizations stay ahead of potential security threats, and ensure compliance with regulations and standards like SSDF.
- Share SBOMs and attestations and monitor risk continuously – Having SBOMs and continuously monitoring potential risks is crucial for maintaining software security and compliance. SBOMs provide consumers with a way to manage risks, detect vulnerabilities, reject low-reputation components, and ensure supply chain security through attestation.
The above four points are the four cornerstones of Software Supply Chain Security and the criteria for choosing a solution in this field.
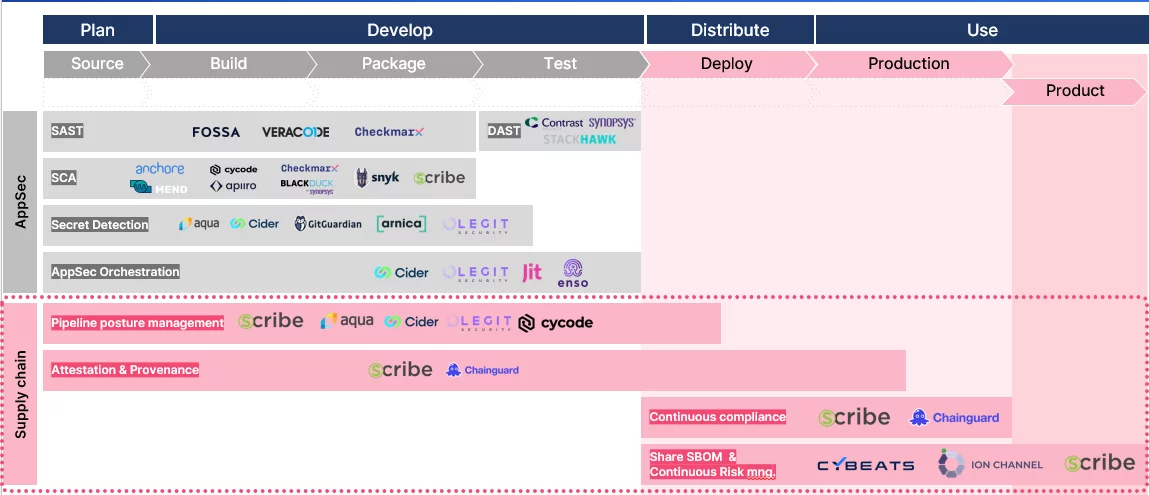
Software Supply Chain Security market landscape about AppSec
Conclusion
As software development and the use of third-party components continue to expand, the need for a comprehensive and integrated approach to software supply chain security has become increasingly important. Traditional AppSec measures are still important but no longer enough to fully protect against the evolving threat landscape, and organizations must adopt a more holistic approach to ensure the security of their software supply chain.
To overcome the evolving security challenges, we are currently witnessing the evolution of application security to software supply chain security. It includes a new generation of technologies and novel tools that try to address these challenges. Software producers need to integrate new security technologies that take advantage of modern frameworks and tools, and they must do so into all stages of the SDLC and use automated tools, such as CI/CD posture management, attestation and provenance technology, continuous code signing, ongoing compliance, and governance, and accurate, high fidelity SBOMs. Software consumers should require SBOMs and further evidence-based attestation to all the security aspects of the software they consume on an ongoing basis, before and after the software deployment to production during its entire life cycle.
Automated tools and solutions like Scribe help organizations achieve a new level of security by providing an evidence-based continuous code security assurance platform that can attest to the trustworthiness of the software development life cycle and software components.
For the complete White Paper click here >>>
This content is brought to you by Scribe Security, a leading end-to-end software supply chain security solution provider – delivering state-of-the-art security to code artifacts and code development and delivery processes throughout the software supply chains. Learn more.



